- BuildMaster
- Getting Started with BuildMaster
- Builds and Continuous Integration
- What is a "Build" in BuildMaster?
- Git and Source Control
- Git Pipelines and Workflows
- Build Scripts & Templates
- Packages & Dependencies
- Build Artifacts
- Automated Testing & Verification
- Deployment & Continuous Delivery
- What is a “Pipeline” in BuildMaster?
- CI Server (Jenkins, TeamCity, etc.) Integration
- Deployment Scripts & Templates
- Automatic Checks & Approval Gates
- Manual Deployment Steps and Tasks
- Databases
- Configuration Files
- Rollbacks
- Advanced CD Patterns
- Applications & Releases
- Connecting to your Servers with BuildMaster
- Scripting in BuildMaster
- Configuring for Your Team
- Docker/Containers
- Development Platforms
- Deployment Targets
- Tools & Service Integrations
- Reference
- BuildMaster API Endpoints & Methods
- Extending BuildMaster
- Built-in Functions & Variables
- Applications
- Builds
- Configuration Files
- Containers
- Credentials
- Databases
- Environments
- Executions
- Files
- General
- JSON
- Linux
- Lists
- Maps
- Math
- Nuget
- Packages
- Pipelines
- PowerShell
- Python
- Releases
- Servers
- Strings
- XML
- Built-in Operations
- Batch
- BuildMaster
- Configuration Files
- Databases
- DotNet
- Files
- Firewall
- General
- Apply-Template
- Attach Package
- Build
- Checkout-Code
- Close-Issue
- Concatenate-Files
- Copy-Files
- Create-Directory
- Create-File
- Create-Issue
- Create-Issue
- Create-IssueComment
- Create-Package
- Create-ZipFile
- Delete-Files
- Download-Asset
- Download-Http
- Ensure-Directory
- Ensure-File
- Ensure-HostsEntry
- Ensure-Metadata
- Ensure-Milestone
- Ensure-Package
- Ensure-Release
- Ensure-Tag
- Exec
- Execute Python Script
- Execute VSTest Tests
- Get-Http
- Install-Package
- OSCall
- OSExec
- Post-Http
- Push-PackageFile
- PYCall
- PYEnsure
- Query-Package
- Remediate-Drift
- Rename-File
- Repackage
- Replace-Text
- Send-Email
- Set-FileAttributes
- Set-Variable
- SHEnsure
- Sleep
- Transfer-Files
- Transition-Issues
- Upload-Assets
- Upload-Http
- Upload-ReleaseAssets
- Git
- IIS
- Nuget
- PowerShell
- ProGet
- Python
- Registry
- Servers
- Services
- Shell
- Windows
- Administration
- Installation & Upgrading
- ProGet
- Getting Started with ProGet
- Packages: Managing & Tracking
- Feeds Types & Third-Party Packages
- What is a "Feed" in ProGet?
- What is a "Connector" in ProGet?
- NuGet (.NET)
- Universal Feeds & Packages
- PowerShell
- Chocolatey (Windows/Machine)
- RubyGems (ruby)
- Visual Studio Extension (.vsix)
- Maven (Java)
- npm (Node.js)
- Bower (JavaScript)
- Debian (Apt)
- Helm (Kubernetes)
- PyPI (Python)
- Conda (Python)
- RPM (Yum)
- Alpine (APK)
- CRAN (R)
- pub (Dart/Flutter)
- Cargo (Rust)
- Terraform Modules
- Conan (C++)
- Composer (PHP)
- Other Feed Types
- Asset Directories & File Storage
- Docker and Containers
- Replication & Feed Mirroring
- Software Composition Analysis (SCA)
- Security and Access Controls
- Cloud Storage
- Administration
- Installation & Upgrading
- API Methods and CLI Commands
- Otter
- Getting Started with Otter
- Orchestration & Server Automation
- Connecting to your Servers with Otter
- Collecting & Verifying Configuration
- Drift Remediation / Configuration as Code
- Scripting in Otter
- Configuring for Your Team
- Installation & Upgrading
- Administration & Maintenance
- Reference
- Otter API Reference
- OtterScript Reference
- Built-in Functions & Variables
- Executions
- Files
- General
- JSON
- Linux
- Lists
- Maps
- Math
- PowerShell
- Python
- Servers
- Strings
- XML
- Built-in Operations
- Batch
- Docker
- DotNet
- Files
- Firewall
- General
- Apply-Template
- Collect Debian Packages
- Collect RPM Packages
- Collect-InstalledPackages
- Concatenate-Files
- Copy-Files
- Create-Directory
- Create-File
- Create-Package
- Create-ZipFile
- Delete-Files
- Download-Asset
- Download-Http
- Ensure-Directory
- Ensure-File
- Ensure-HostsEntry
- Ensure-Metadata
- Ensure-Package
- Exec
- Execute Python Script
- Get-Http
- Install-Package
- OSCall
- OSExec
- Post-Http
- Push-PackageFile
- PYCall
- PYEnsure
- Query-Package
- Remediate-Drift
- Rename-File
- Repackage
- Replace-Text
- Send-Email
- Set-FileAttributes
- Set-Variable
- SHEnsure
- Sleep
- Transfer-Files
- Upload-Assets
- Upload-Http
- IIS
- Otter
- PowerShell
- ProGet
- Python
- Registry
- Servers
- Services
- Shell
- Windows
- Installation & Maintenance
- Windows (Inedo Hub)
- Linux (Docker)
- High Availability & Load Balancing
- User Directories & Domains (LDAP)
- Logging & Analytics
- SAML Authentication
- When to Upgrade your Inedo Product
- Managing Agents and Servers
- Backing Up & Restoring
- Installation Configuration Files
- PostgreSQL & Inedo Products
- SQL Server & Inedo Products
- Inedo Agent
- What is the Inedo Agent?
- Installation & Upgrading
- Downloads & Release Notes
- Maintenance & Configuration
- Internal Architecture
- MyInedo
- OtterScript (Execution Engine)
- Reference
- OtterScript
- Inedo Execution Engine
- Romp (Discontinued)
- Using Romp
- Installing, Configuring, and Maintaining
- Romp CLI Reference
- Package Layout
- Downloads & Source Code
- Extensibility
- Inedo SDK
Deprecated: WhiteSourcePackage Access Rules
This article is for users who have configured Whitesource integration or created their own Package Access Rules and wish to explore alternative options in ProGet 2024.
In the many years since we launched ProGet's WhiteSource integration, both products have evolved quite a bit:
- Whitesource became Mend.io and no longer supports integrations created by third-parties like our integration
- ProGet introduced a whole host of license management, vulnerability detection, and compliance detection that are generally rated better than Mend.io's offering
In that same time, we couldn't find any other use cases for the "Package Access Rules" extensibility point that we added to ProGet. As such, both are discontinued in ProGet 2024. If you'd like to view our old documentation on how to integrate the producs, check out How to Integrate ProGet with WhiteSource (archive.org).
WhiteSource (Mend.io) Alternatives
The primary use case for using WhiteSource with ProGet was to define policies that would restrict access to specific packages based on license type and vulnerability severity. Compared to ProGet 2023 and earlier versions, WhiteSource's project- and organization-level projects were more robust and offered more flexibility than ProGet's vunlerability and licensing blocking rules.
However, the Policies & Compliance Rules feature introduced ProGet 2024 flipped the script. Now, ProGet's policies are more robust and offer more flexibility than WhiteSource policies.
In addition, instead of getting a "Package Blocked by WhiteSource" message, and then having to hunt down and debug the relevant WhiteSource policies, you can get a clear message in ProGet showing exactly why the package is blocked:
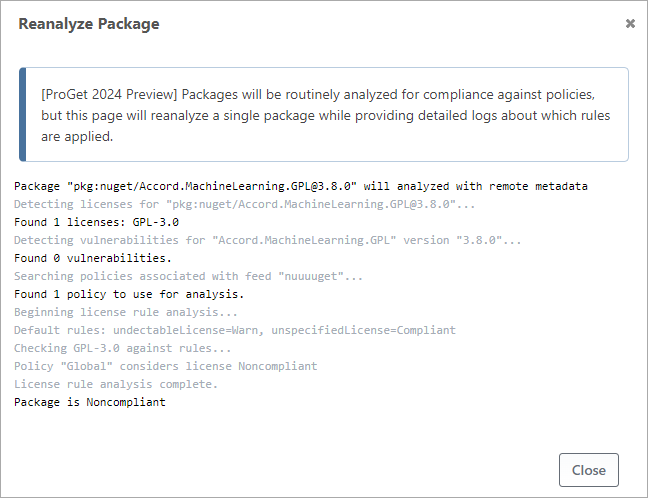
ProGet's policies also work with remote packages, while WhiteSource was limited to local/cached packages - which meant you'd have to download a package to determine if it's compliant.
Package Access Rule Alternatives
To integrate with WhiteSource, we created an extensible component called a PackageAccessRule that could be associated with a feed. It was very simple:
- Input: Package Identifier (i.e. Name, Version)
- Output: Blocked (Yes/No) and Reason (Text)
With ProGet 2024's policy-based model, this component no longer makes sense. Packages are no longer "blocked", but are Compliant, Noncompliant, or Warn - and a feed then determines if Noncompliant packages are blocked from being downloaded.
In addition, with WhiteSource being discontinued, there's no use case for this extensibility feature. We're not aware of any users who created an extension with a Package Access Rule.
That being said, we could definitely see some utility in creating a custom compliance rule, that would work similar to a PackageAccessRule, but would instead of Blocked would output Compliant, Noncompliant, or Warn. However, before adding that, we'd like to hear from users on what sort of custom rules they would want to develop.
If you're interested in this, just contact us via the support channel and we'll go from there.

