- BuildMaster
- Getting Started with BuildMaster
- Builds and Continuous Integration
- What is a "Build" in BuildMaster?
- Git and Source Control
- Git Pipelines and Workflows
- Build Scripts & Templates
- Packages & Dependencies
- Build Artifacts
- Automated Testing & Verification
- Deployment & Continuous Delivery
- What is a “Pipeline” in BuildMaster?
- CI Server (Jenkins, TeamCity, etc.) Integration
- Deployment Scripts & Templates
- Automatic Checks & Approval Gates
- Manual Deployment Steps and Tasks
- Databases
- Configuration Files
- Rollbacks
- Advanced CD Patterns
- Applications & Releases
- Connecting to your Servers with BuildMaster
- Scripting in BuildMaster
- Configuring for Your Team
- Docker/Containers
- Development Platforms
- Deployment Targets
- Tools & Service Integrations
- Reference
- BuildMaster API Endpoints & Methods
- Extending BuildMaster
- Built-in Functions & Variables
- Applications
- Builds
- Configuration Files
- Containers
- Credentials
- Databases
- Environments
- Executions
- Files
- General
- JSON
- Linux
- Lists
- Maps
- Math
- Nuget
- Packages
- Pipelines
- PowerShell
- Python
- Releases
- Servers
- Strings
- XML
- Built-in Operations
- Batch
- BuildMaster
- Configuration Files
- Databases
- DotNet
- Files
- Firewall
- General
- Apply-Template
- Attach Package
- Build
- Checkout-Code
- Close-Issue
- Concatenate-Files
- Copy-Files
- Create-Directory
- Create-File
- Create-Issue
- Create-Issue
- Create-IssueComment
- Create-Package
- Create-ZipFile
- Delete-Files
- Download-Asset
- Download-Http
- Ensure-Directory
- Ensure-File
- Ensure-HostsEntry
- Ensure-Metadata
- Ensure-Milestone
- Ensure-Package
- Ensure-Release
- Ensure-Tag
- Exec
- Execute Python Script
- Execute VSTest Tests
- Get-Http
- Install-Package
- OSCall
- OSExec
- Post-Http
- Push-PackageFile
- PYCall
- PYEnsure
- Query-Package
- Remediate-Drift
- Rename-File
- Repackage
- Replace-Text
- Send-Email
- Set-FileAttributes
- Set-Variable
- SHEnsure
- Sleep
- Transfer-Files
- Transition-Issues
- Upload-Assets
- Upload-Http
- Upload-ReleaseAssets
- Git
- IIS
- Nuget
- PowerShell
- ProGet
- Python
- Registry
- Servers
- Services
- Shell
- Windows
- Administration
- Installation & Upgrading
- ProGet
- Getting Started with ProGet
- Packages: Managing & Tracking
- Feeds Types & Third-Party Packages
- What is a "Feed" in ProGet?
- What is a "Connector" in ProGet?
- NuGet (.NET)
- Universal Feeds & Packages
- PowerShell
- Chocolatey (Windows/Machine)
- RubyGems (ruby)
- Visual Studio Extension (.vsix)
- Maven (Java)
- npm (Node.js)
- Bower (JavaScript)
- Debian (Apt)
- Helm (Kubernetes)
- PyPI (Python)
- Conda (Python)
- RPM (Yum)
- Alpine (APK)
- CRAN (R)
- pub (Dart/Flutter)
- Cargo (Rust)
- Terraform Modules
- Conan (C++)
- Composer (PHP)
- Other Feed Types
- Asset Directories & File Storage
- Docker and Containers
- Replication & Feed Mirroring
- Software Composition Analysis (SCA)
- Security and Access Controls
- Cloud Storage
- Administration
- Installation & Upgrading
- API Methods and CLI Commands
- Otter
- Getting Started with Otter
- Orchestration & Server Automation
- Connecting to your Servers with Otter
- Collecting & Verifying Configuration
- Drift Remediation / Configuration as Code
- Scripting in Otter
- Configuring for Your Team
- Installation & Upgrading
- Administration & Maintenance
- Reference
- Otter API Reference
- OtterScript Reference
- Built-in Functions & Variables
- Executions
- Files
- General
- JSON
- Linux
- Lists
- Maps
- Math
- PowerShell
- Python
- Servers
- Strings
- XML
- Built-in Operations
- Batch
- Docker
- DotNet
- Files
- Firewall
- General
- Apply-Template
- Collect Debian Packages
- Collect RPM Packages
- Collect-InstalledPackages
- Concatenate-Files
- Copy-Files
- Create-Directory
- Create-File
- Create-Package
- Create-ZipFile
- Delete-Files
- Download-Asset
- Download-Http
- Ensure-Directory
- Ensure-File
- Ensure-HostsEntry
- Ensure-Metadata
- Ensure-Package
- Exec
- Execute Python Script
- Get-Http
- Install-Package
- OSCall
- OSExec
- Post-Http
- Push-PackageFile
- PYCall
- PYEnsure
- Query-Package
- Remediate-Drift
- Rename-File
- Repackage
- Replace-Text
- Send-Email
- Set-FileAttributes
- Set-Variable
- SHEnsure
- Sleep
- Transfer-Files
- Upload-Assets
- Upload-Http
- IIS
- Otter
- PowerShell
- ProGet
- Python
- Registry
- Servers
- Services
- Shell
- Windows
- Installation & Maintenance
- Windows (Inedo Hub)
- Linux (Docker)
- High Availability & Load Balancing
- User Directories & Domains (LDAP)
- Logging & Analytics
- SAML Authentication
- When to Upgrade your Inedo Product
- Managing Agents and Servers
- Backing Up & Restoring
- Installation Configuration Files
- PostgreSQL & Inedo Products
- SQL Server & Inedo Products
- Inedo Agent
- What is the Inedo Agent?
- Installation & Upgrading
- Downloads & Release Notes
- Maintenance & Configuration
- Internal Architecture
- MyInedo
- OtterScript (Execution Engine)
- Reference
- OtterScript
- Inedo Execution Engine
- Romp (Discontinued)
- Using Romp
- Installing, Configuring, and Maintaining
- Romp CLI Reference
- Package Layout
- Downloads & Source Code
- Extensibility
- Inedo SDK
Deprecated: Clair and ProGet
This article is for users who have configured ProGet's Clair integration and wish to learn how to switch to ProGet's built-in container scanning feature. If you haven't configured container scanning and vulnerability scanning in ProGet yet, check out HOWTO: Scan and Block Packages in ProGet to learn more.
ProGet no longer relies on Clair, the third-party container-scanning tool, to find vulnerabilities in containers. Instead, this functionality is built-in, and uses industry-leading vulnerability scanning and detection from our own Inedo Security Labs.
If you're using ProGet 2023 and earlier, you're welcome to follow the archived guide for Clair integration, but we recommend upgrading ProGet and using new features instead.
Clair vs ProGet's Built-in Container Scanning
Prior to 2023.29, ProGet did not have container scanning capabilities. Instead, we relied on a free and open-source tool called Clair to perform this function. Clair is a standalone, third-party tool that is somewhat complex to configure and requires additional resources to run and manage.
As a standalone tool, one of the main issues is that containers needed to be uploaded to Clair on a nightly basis. This meant vulnerability detection was often delayed, and both Clair and ProGet would be taxed during the nightly scan.
In contrast, ProGet's built-in container scanning happens immediately after upload. Instead of needing to scan a container multiple times for packages, ProGet "remembers" which packages a container has - and can then easily detect vulnerabilities in those packages.
Migrating from Clair to ProGet's Vulnerability Database
To migrate from Clair, you simply need to delete the Clair vulnerability source and enable ProGet 2024 Preview Vulnerability features.
First, navigate to "Administration Overview" > "Vulnerabilities Sources" under "Vulnerability Management".
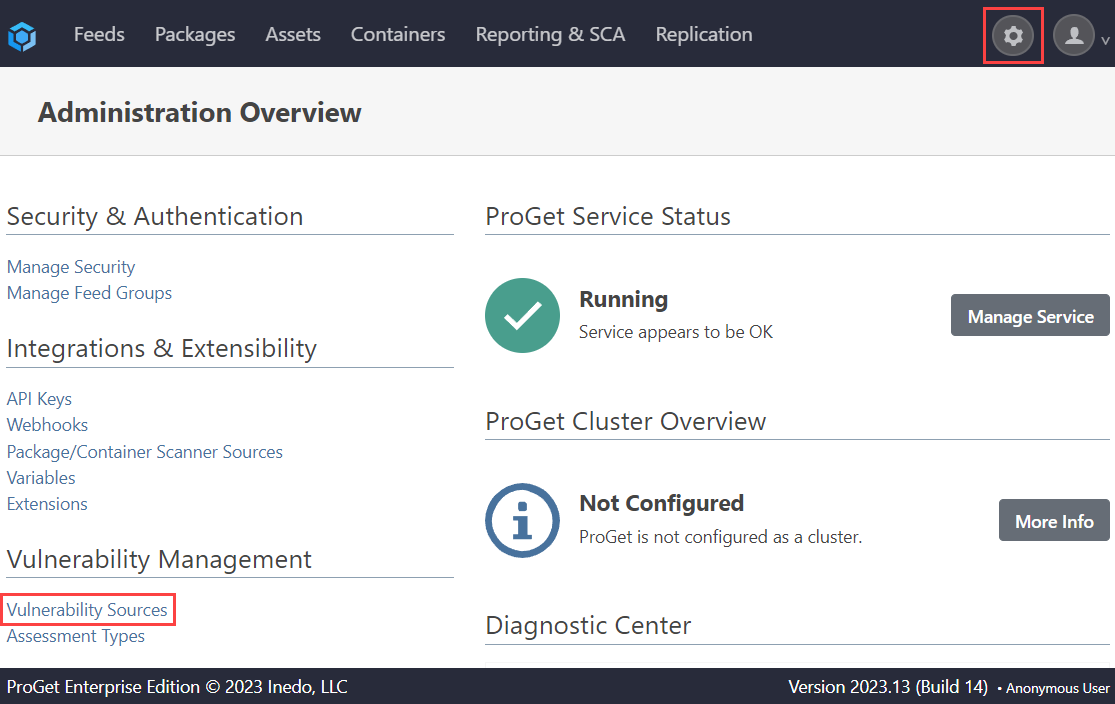
From here, delete the Clair entry.
However, if your assessment types are configured for automatic assessment, then vulnerabilities detected in containers will be automatically assessed after the container is scanned.
Next, navigate to "Reporting & SCA" > "Vulnerabilities" and select "Enable Vulnerabilities Feature Preview..."
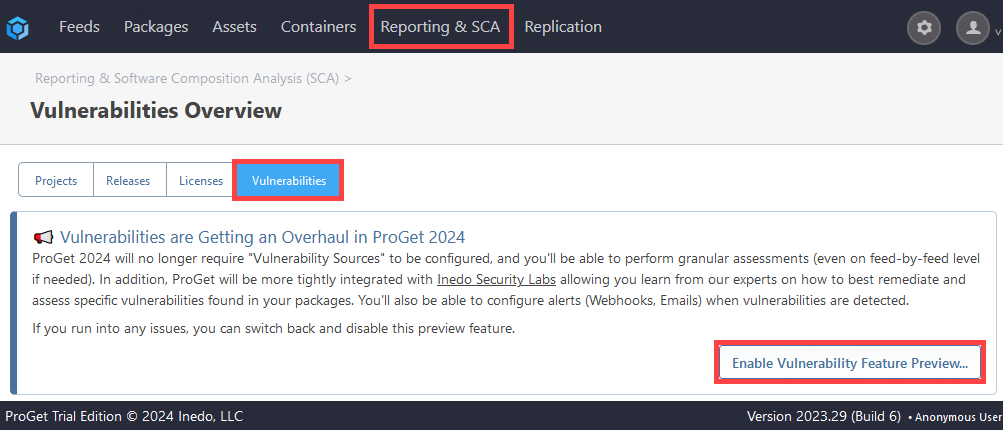
Enabling the Preview Feature will also download the latest vulnerability definitions from Inedo Security Labs
Finally, make sure "Layer Scanning" is enabled. Navigate to your Docker feeds, and select "Manage Feed".
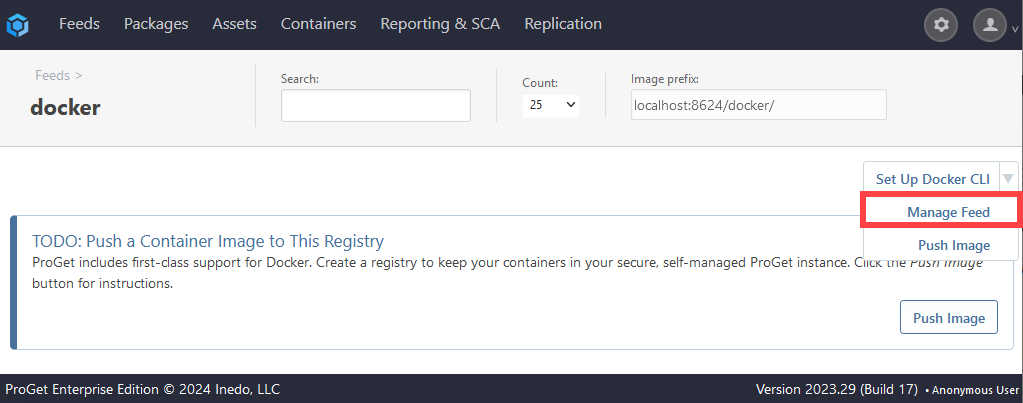
Then, navigate to "Layer Scanning":
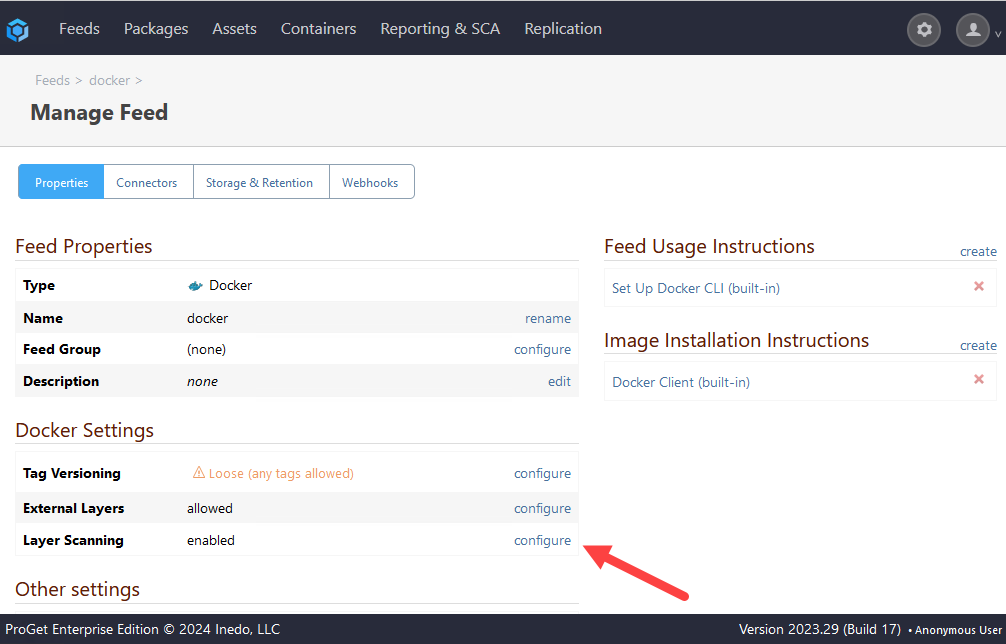
If Layer Scanning is disabled, check "Enable layer scanning". ProGet will warn that it may take some time depending on the volume of images in your repository. When you are ready to perform this scan, select "Save".
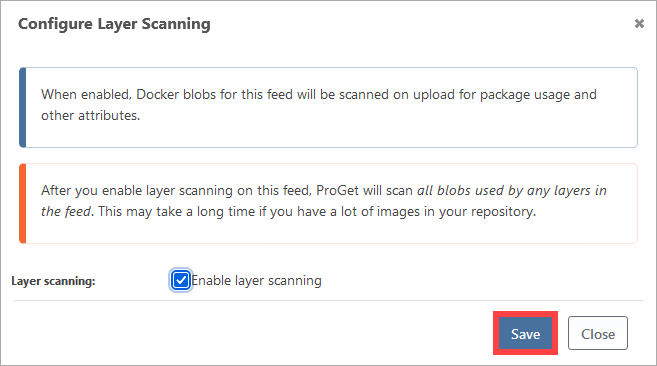
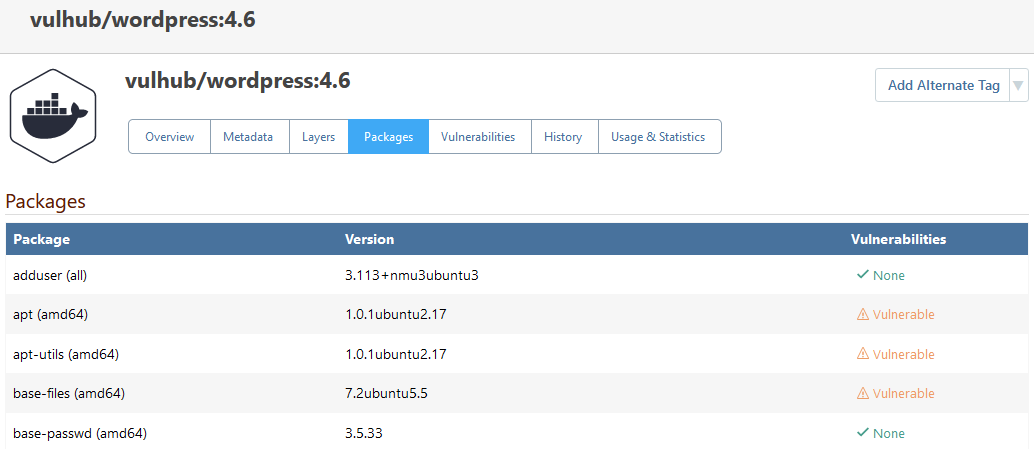
To scan containers for vulnerabilities, ProGet extracts and inspects the files within each container image layer and looks for vulnerable packages that are installed. After the scan, the "Packages" and "Vulnerabilities" tab of a container image will show these: